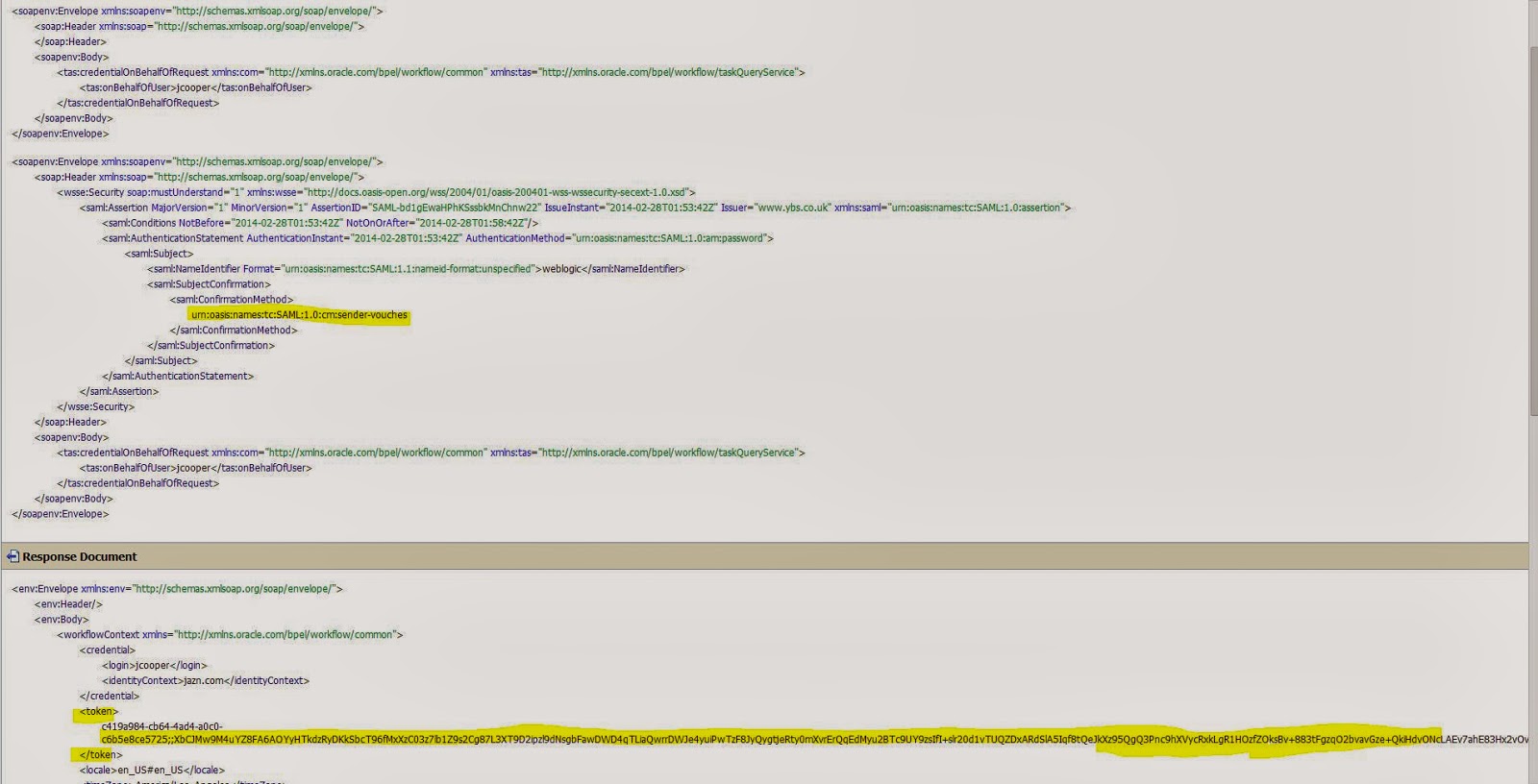
Scenario: - Invoke task query service securely by using
wss10_saml_token_client_policy OWSM policy and CSF key. Without inbound subject(Principal)
Solution:
You can find sample BPEL project on Task Query service using SAML on Jeroren Bakker's blog .This blog based on policy's default setting like "subject.precedence" = true which means policy expect subject (Principal) from inbound.
You can use same project but with following settings.
BPEL
. 1. Create "basic.credentials" CSF
key in EM console

2.
Apply wss10_saml_token_client_policy on Task Query
Service in BPEL Process
Edit
policy properties.
·
If there is other issuer than oracle override the
value of “saml.issuer.name” property.
·
Override value of “subject.precedence” to false.
SAML client policy having default "basic.credential" csf key value.
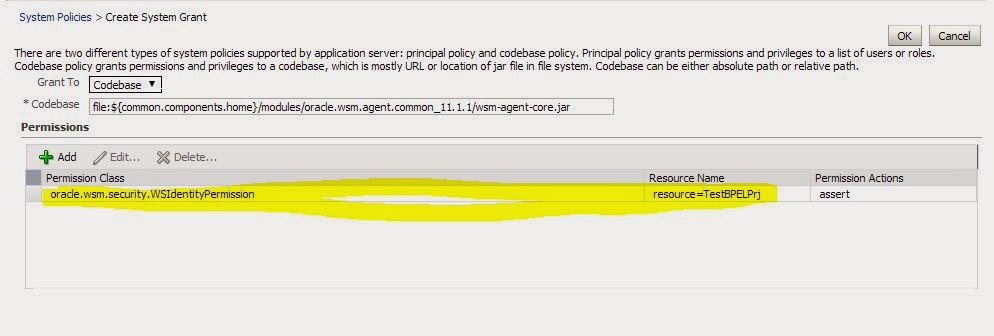
3. If we are using "subject.precendece" option as false, it means we are not using or expecting any inbound subject and we are going to use CSF key to generate SAML token. To accomplish this opertation, we have to give WSIdentityPermission to our SOA project. In my case ,composite name is TaskQuery_Process.
Set the
WSIdentityPermissio
- In the
navigator pane, expand WebLogic Domain
to show the domain where you need to configure the application. Select the
domain.
- Using
Fusion Middleware Control, click WebLogic Domain, then Security, and then System Policies. System policies are
the system-wide
policies applied to all applications deployed to the current WebLogic Domain.
- From the System Policies page, select the arrow
icon in the Permission field to search the system security grants
- Select one
of the codebase permissions to use
as a starting point and click Create Like.
- In the Grant Details section of the page,
enter file:${common.components.home}/modules/oracle.wsm.agent.common_11.1.1/wsm-agent-core.jar
in the Codebase field.
- In the Permissions section of the page, select
the starting point permission class and click Edit.
- Enter oracle.wsm.security.WSIdentityPermission
in the Permission Class field. The resource name is the composite name for SOA,
and the application name for a J2EE client. The action is always assert.
Restart your SOA server.
After restart you can test you task query service from BPEL by using SAML port.
OSB
- We have to perform same configuration for OSB business
service.
-
Set “subject.precedence” value to false.
- Override "saml-issuer-name" property if its other than oracle.
OSB Request- Remove "workflowContext" element from the request.
TaskQuery Service Method - authenticateOnBehalfOf