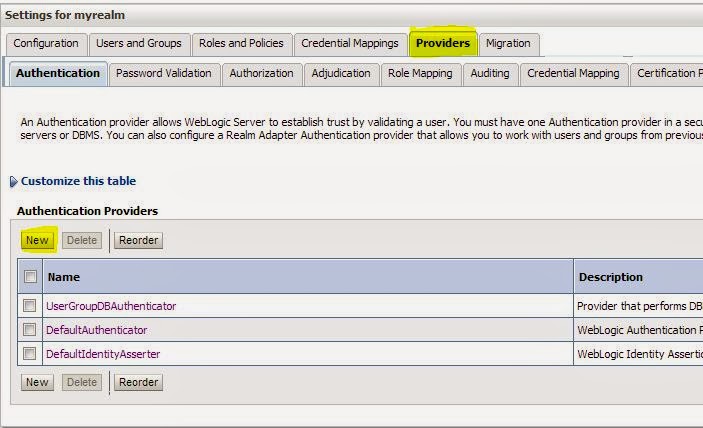
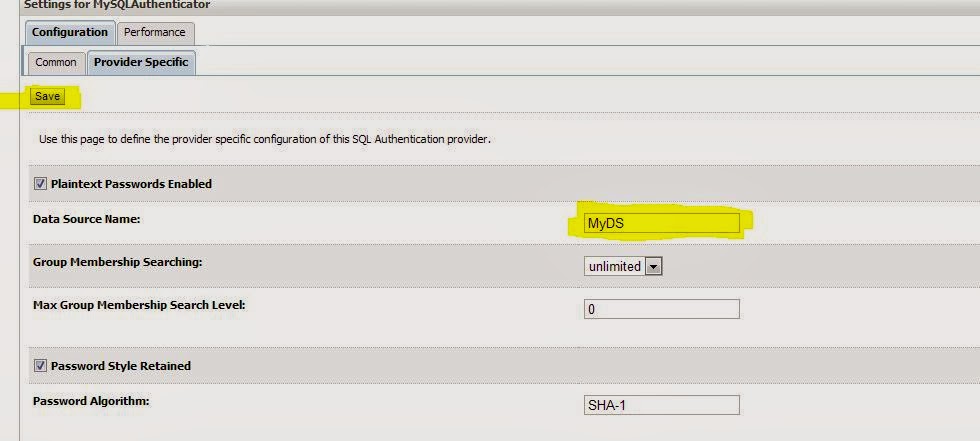
Please refer my previous blog to know how to configure SQL Authenticator
Configure SQL Authenticator
Please follow these steps
Changed default realm
(EM Console)Changed the value of key
“WorkflowIdentityConfig.ConfigurationType” from default “jazn.com” to “myrealm”
by executing the “setRealmName” operation
soa-infra ->Administration -> System Mbean Browser -> Application Defined Mbeans - > oracle.as.soainfra.config -> Server - > WorkflowIdentityConfig -> human-workflow -> WorkflowIdentityConfig.ConfigurationType -> select the configuration and rename by invoking the operation setRealmName
SQL
Authenticator Configuration for BPM worklist and Human Task Flow
Download the attachment: workflow-120-SQLIdentityProvider.zip
Copy dbprovider.jar from
workflow-120-SQLIdentityProvider\lib to MW_HOME/user_projects/domains/{soa_domain}/lib
Follow the steps
below:
1. Shutdown SOA and Admin Server
2. Navigate to MW_HOME/user_projects/domains/{domain_name}/config/fmwconfig
3. Backup
jps-config.xml
4. Edit
jps-config.xml and make the following modifications
A. Modify
<serviceInstanceRef
ref="idstore.ldap"/> to
<serviceInstanceRef
ref="idstore.custom"/>
under <jpsContext
name="default">
B. Add
<serviceInstance name="idstore.custom"
provider="custom.provider"
location="dumb">
<description>Custom
Identity Store Service Instance</description>
<property name="idstore.type"
value="CUSTOM"/>
<property
name="ADF_IM_FACTORY_CLASS"
value="org.sample.providers.db.DBIdentityStoreFactory"/>
<property name="DB_SERVER_NAME"
value="db_host_name"/>
<property name="DB_SERVER_PORT"
value="db_port"/>
<property name="DB_DATABASE_NAME"
value="db_sid"/>
<property
name="ST_SECURITY_PRINCIPAL" value="db_user"/>
<property
name="ST_SECURITY_CREDENTIALS" value="db_passwd"/>
</serviceInstance>
under <serviceInstances>
change the db_*
parameters as per the environment
C. Add
<serviceProvider
type="IDENTITY_STORE" name="custom.provider"
class="oracle.security.jps.internal.idstore.generic.GenericIdentityStoreProvider">
<description>Custom
IdStore Provider</description>
</serviceProvider>
within <serviceProviders>
</serviceProviders>
.
5. Start SOA/Admin
server
Now logging on to
worklist application should work.
I have tested this on my local machine and it
works.
6. You can also configure human task from JDeveloper to add user from SQL authenticator.For that realm setting is must as mentioned in "Changed default realm" step.